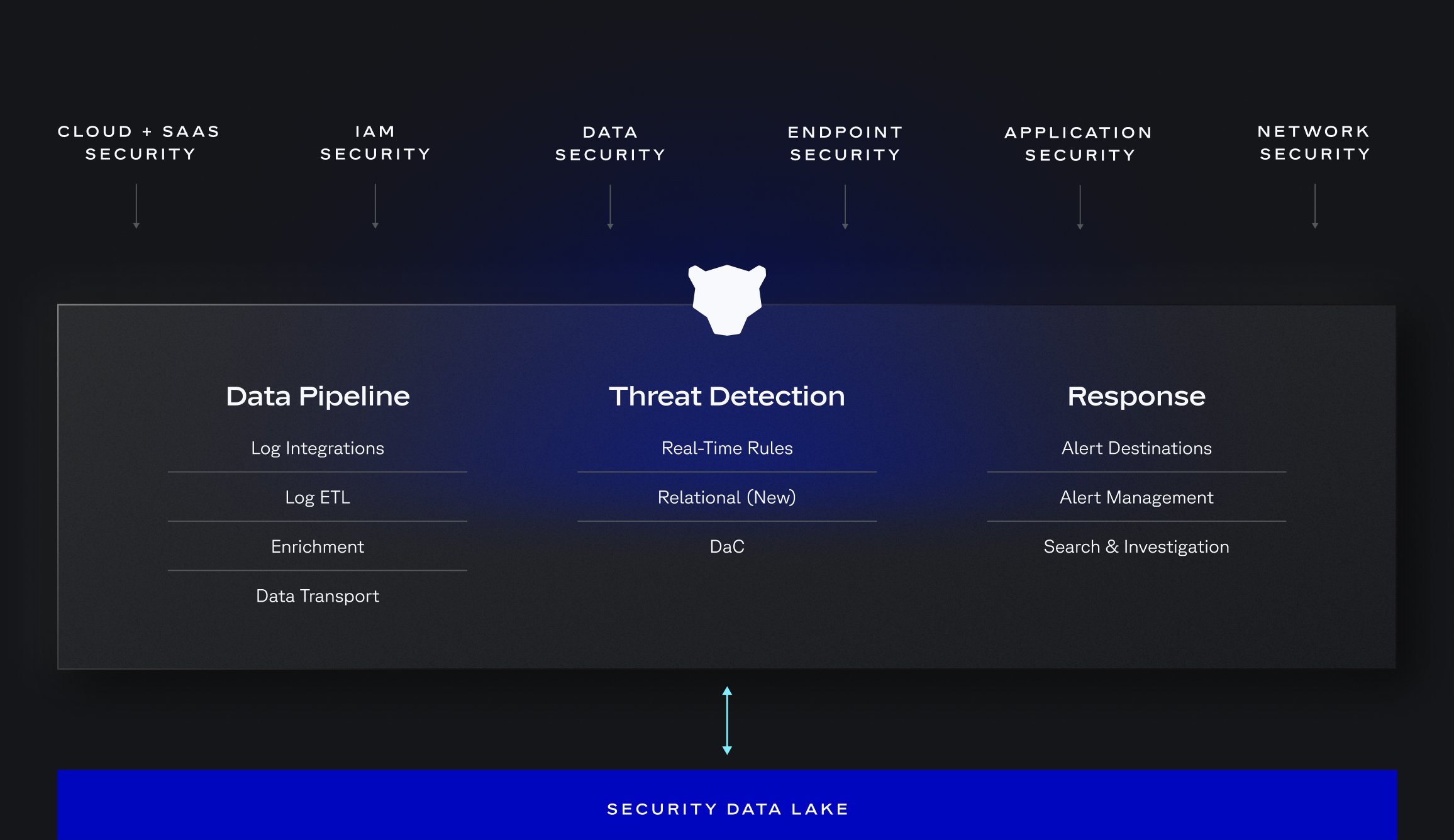
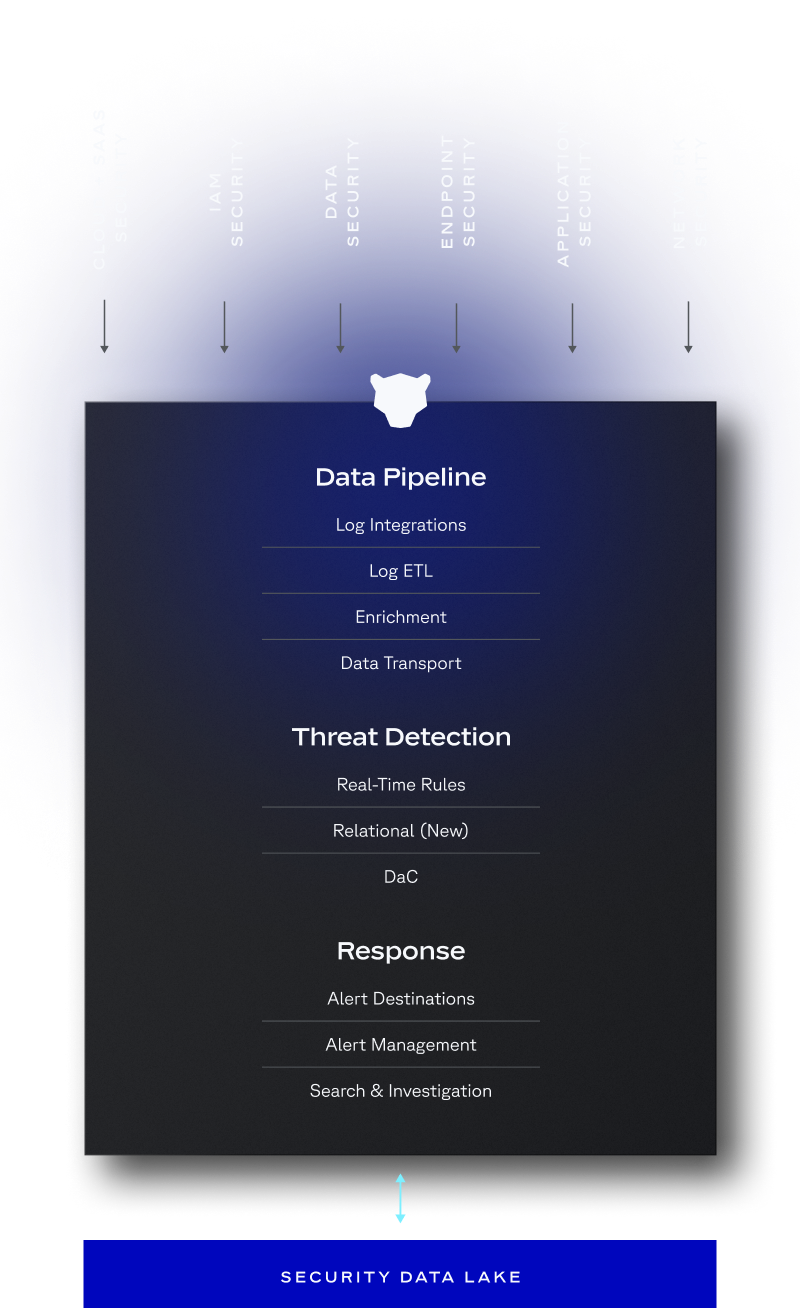
How It Works
Cloud-Native Ecosystem Integrations
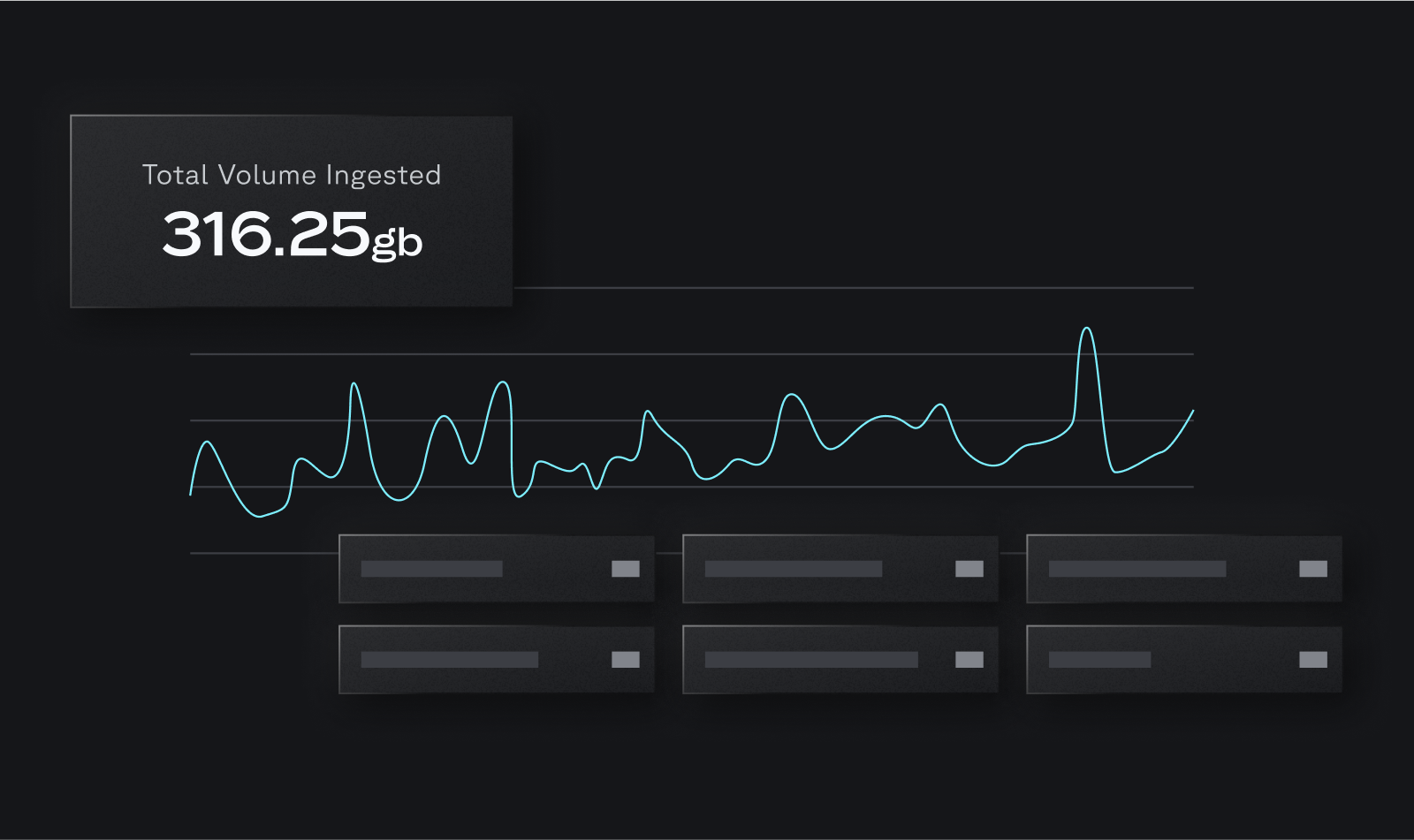
Easily ingest your existing data stack into Panther. Eliminate friction with out-of-the-box integrations for 60+ log types and support for custom data sources.
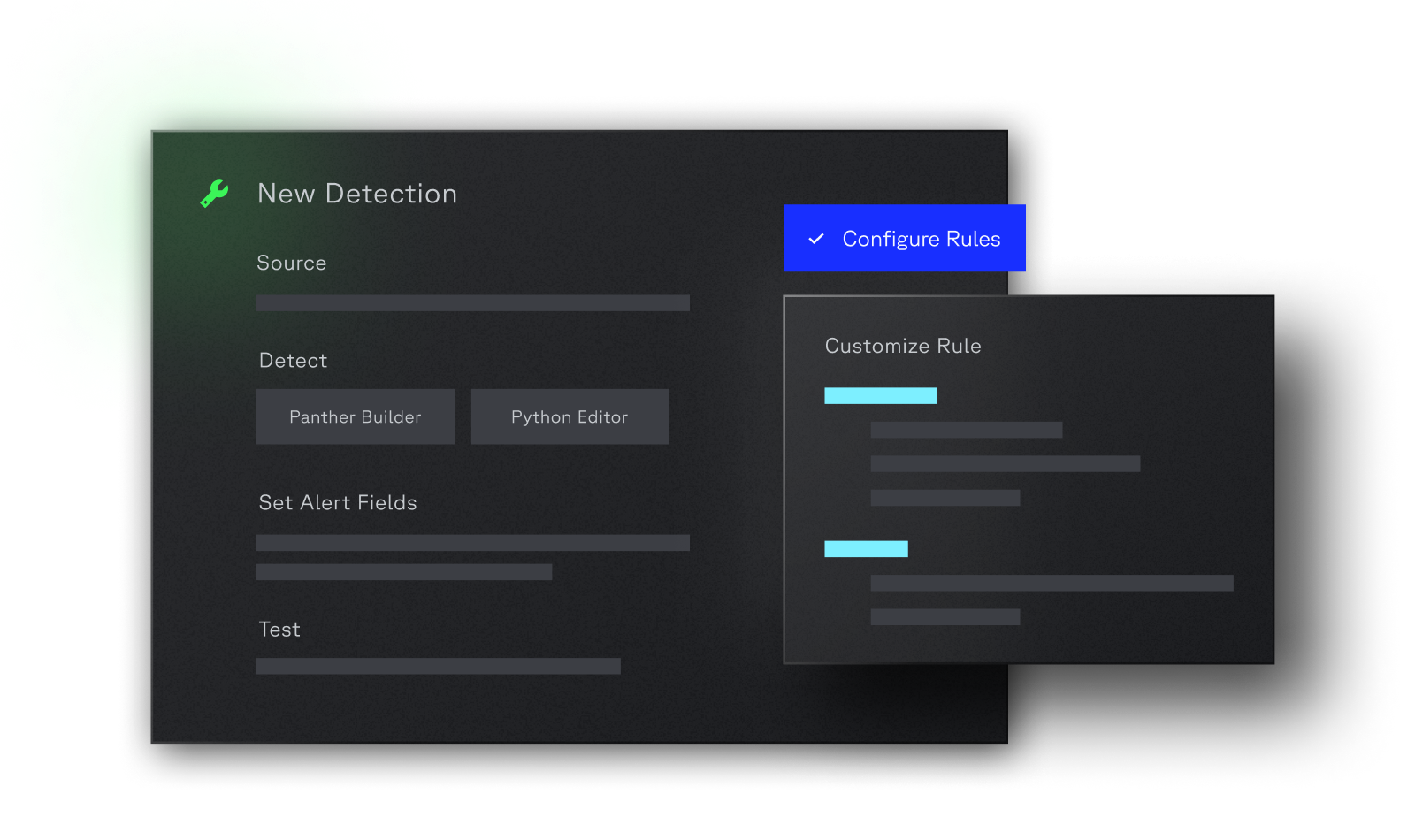
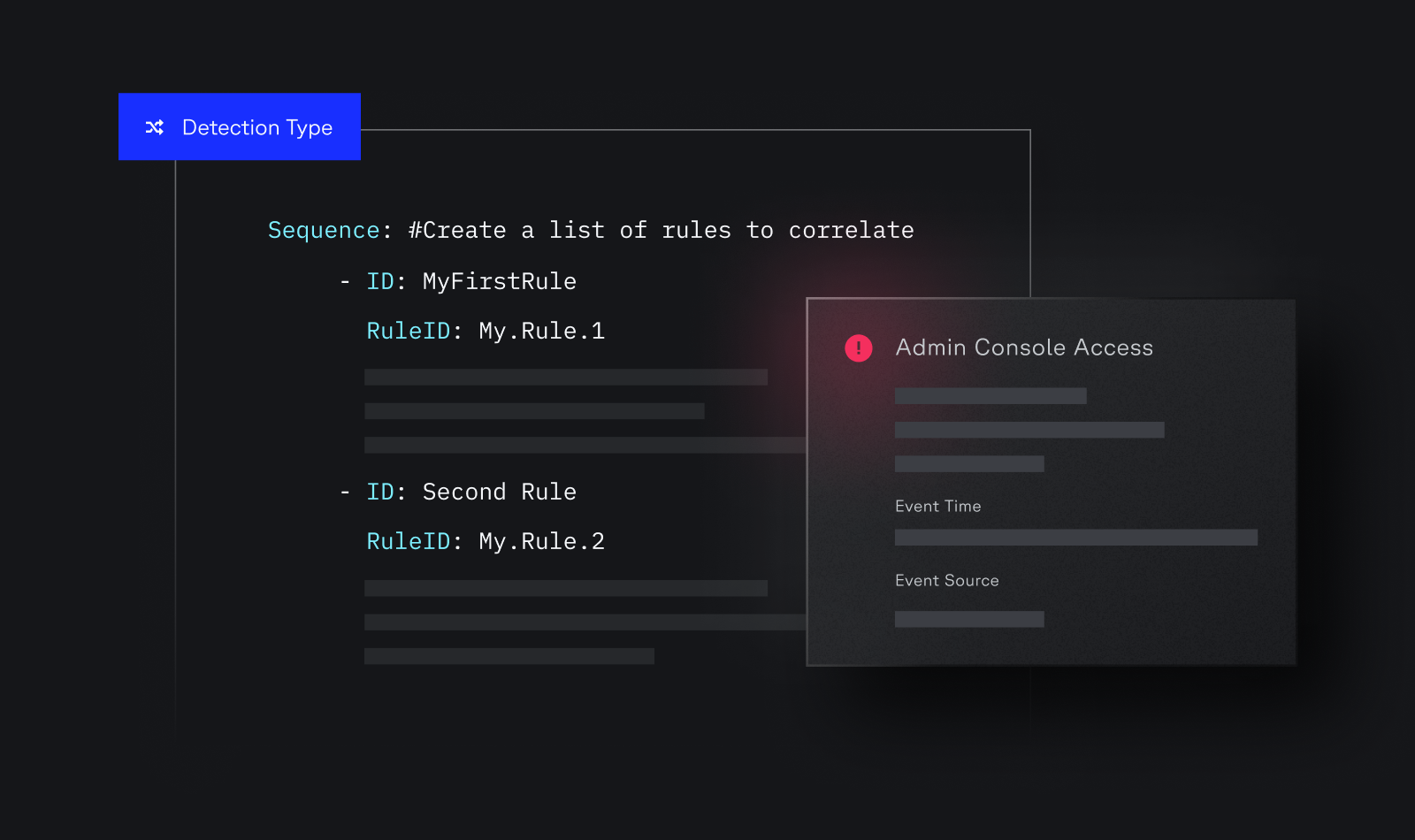
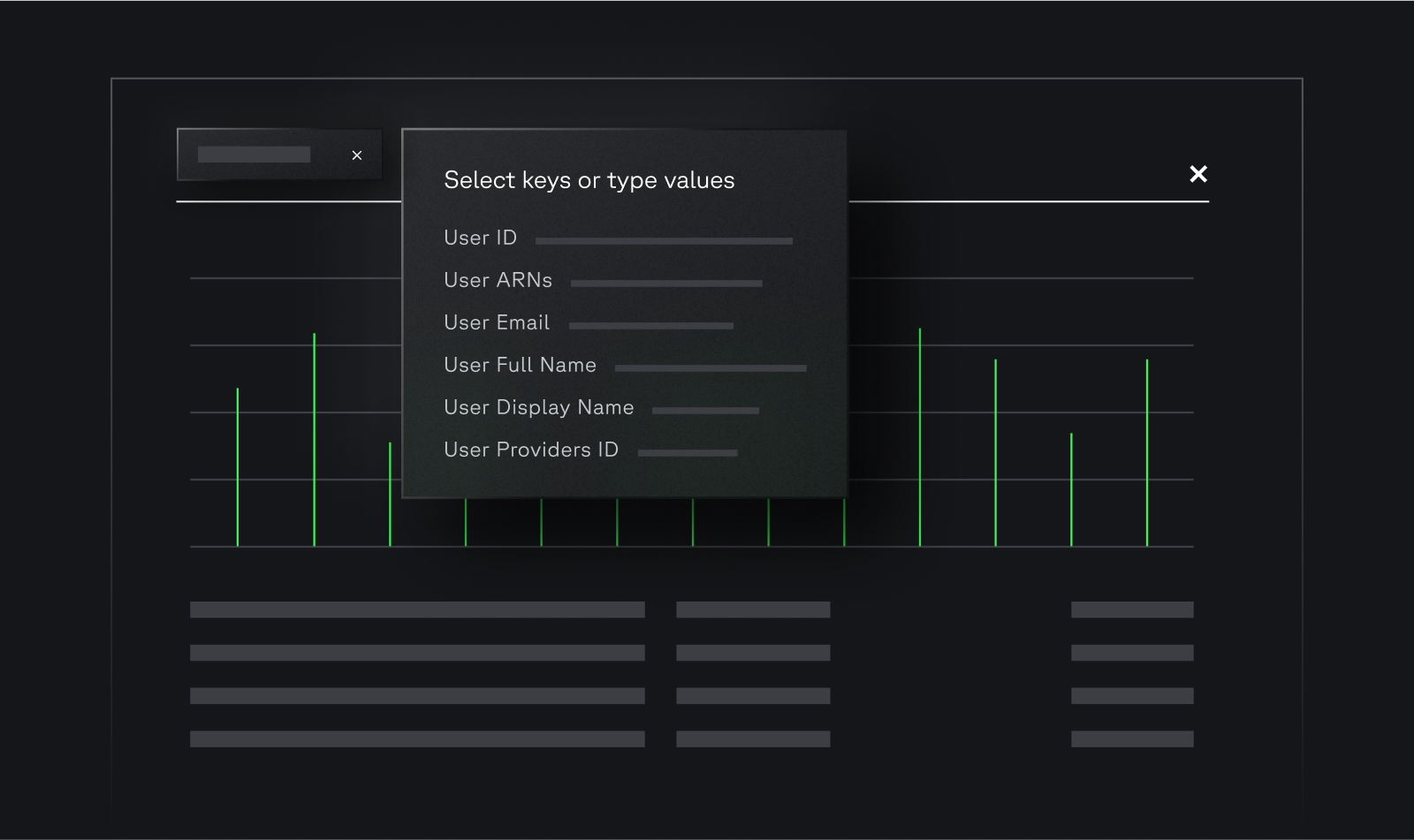
Today’s security landscape demands Code-Driven SecOps. Panther brings detection-as-code, intuitive investigations, and a high-performance platform to distill signal and eliminate noise at cloud scale.








By continuing to use this website you consent to our use of cookies.


