How It Works
Ingest AWS Logs
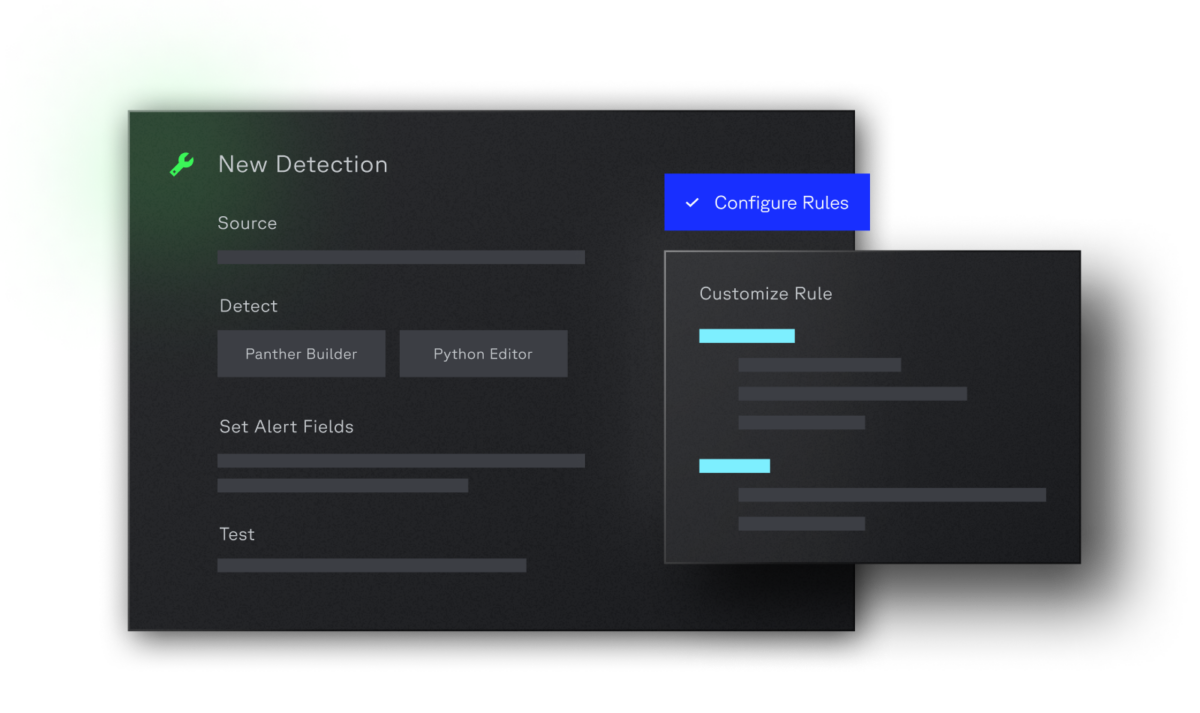
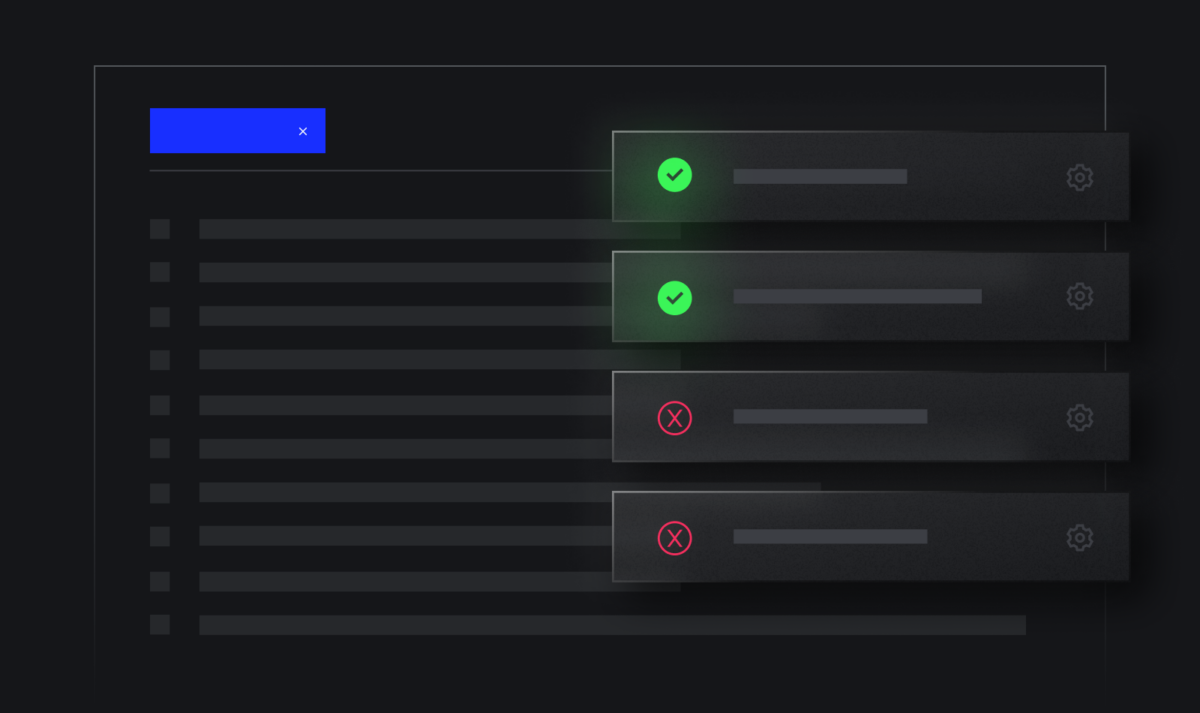
Centralize your AWS logs into one platform with shared visibility across your environment using Panther’s OOTB integrations and pre-built schemas for common AWS services like GuardDuty, Cloudtrail, and EKS. Panther normalizes data upon ingestion, delivering lightning fast query speeds in your investigation and response workflows. The data lake scales effortlessly alongside your growing AWS environment to meet your team’s changing needs, without breaking the budget.