Panther believes firmly in the power of Detection-as-Code. In the past, this meant we focused primarily on building a tool for security engineers with deep coding experience. While Panther will continue to place the developer workflow at the heart of our experience, we also want to unlock the value of Detection-as-Code for everyone. A key part of this vision is enabling teams with varying levels of development experience to effectively build, manage, and collaborate on their detection logic.
Currently, Panther’s detections are powered by Python, which provides an exceptional level of flexibility and power for identifying suspicious activity in your environment.
However, we understand that this level of sophistication is not always necessary. To augment the user experience for creating and managing detections, Panther is actively developing a simpler interface for writing and modifying detections.
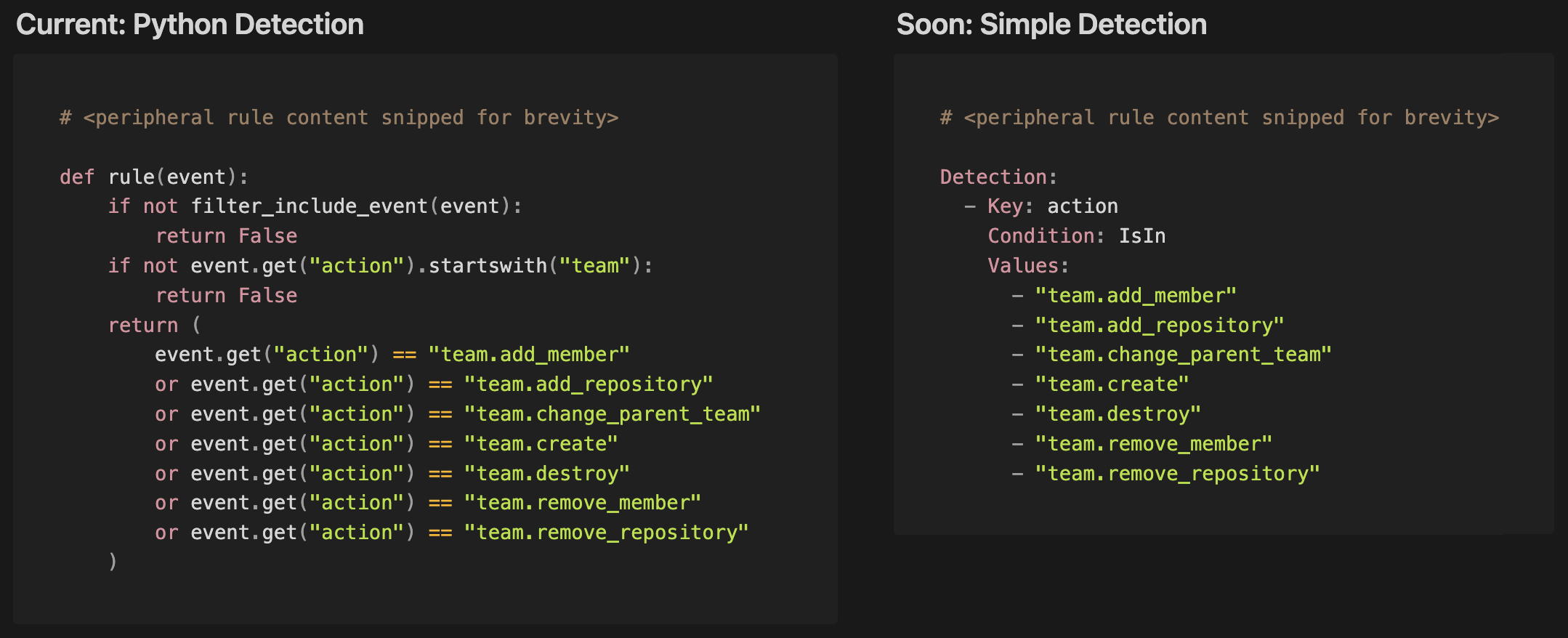
Soon, most of the Panther-managed detections will be available in a simple human-readable description language, YAML. Below is an example rule that detects when a team is modified in GitHub. You can see how the Python rule (left) easily translates into a YAML-based rule (right). A key benefit of YAML-based detection logic is that it preserves the benefits of detection-as-code while also simplifying how rules are expressed.
We will also continue to fully support Python detections. Certain more complex detections, in fact, require the expressiveness offered by Python.
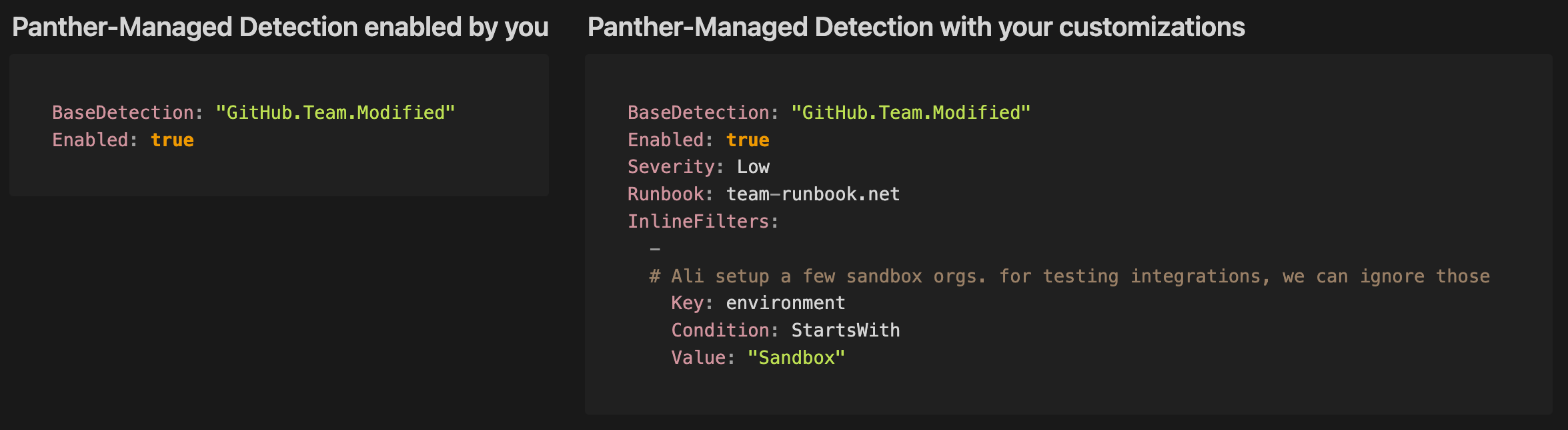
Simple Detections also enables an inheritance model for detection logic. This means when you’re using Panther-managed YAML detections, Panther’s core rule logic will be stored in a separate file from your customizations, which simply reference the base rule. A key benefit of the inheritance model is that upgrades to Panther-managed detection logic will be seamlessly applied across customer environments. We’re excited about the implications for code reuse and extension flexibility this new structure brings.
Customer-maintained YAML-based detections:
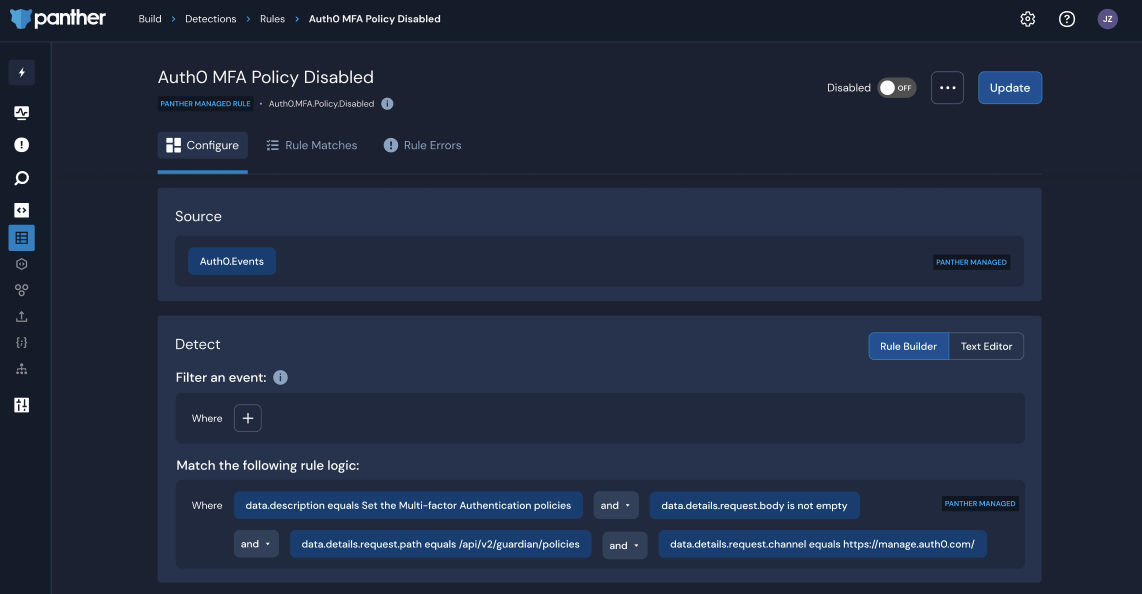
In the Console, analysts will be able to read, modify, and write detections using a GUI builder to express detections in a YAML-based format. You can tailor a Panther-managed rule by adding a filter using the form builder or text-based editor. Additionally, you can create and deploy brand-new detections using a similar experience.
Configure a detection:
Configure dynamic alert fields:
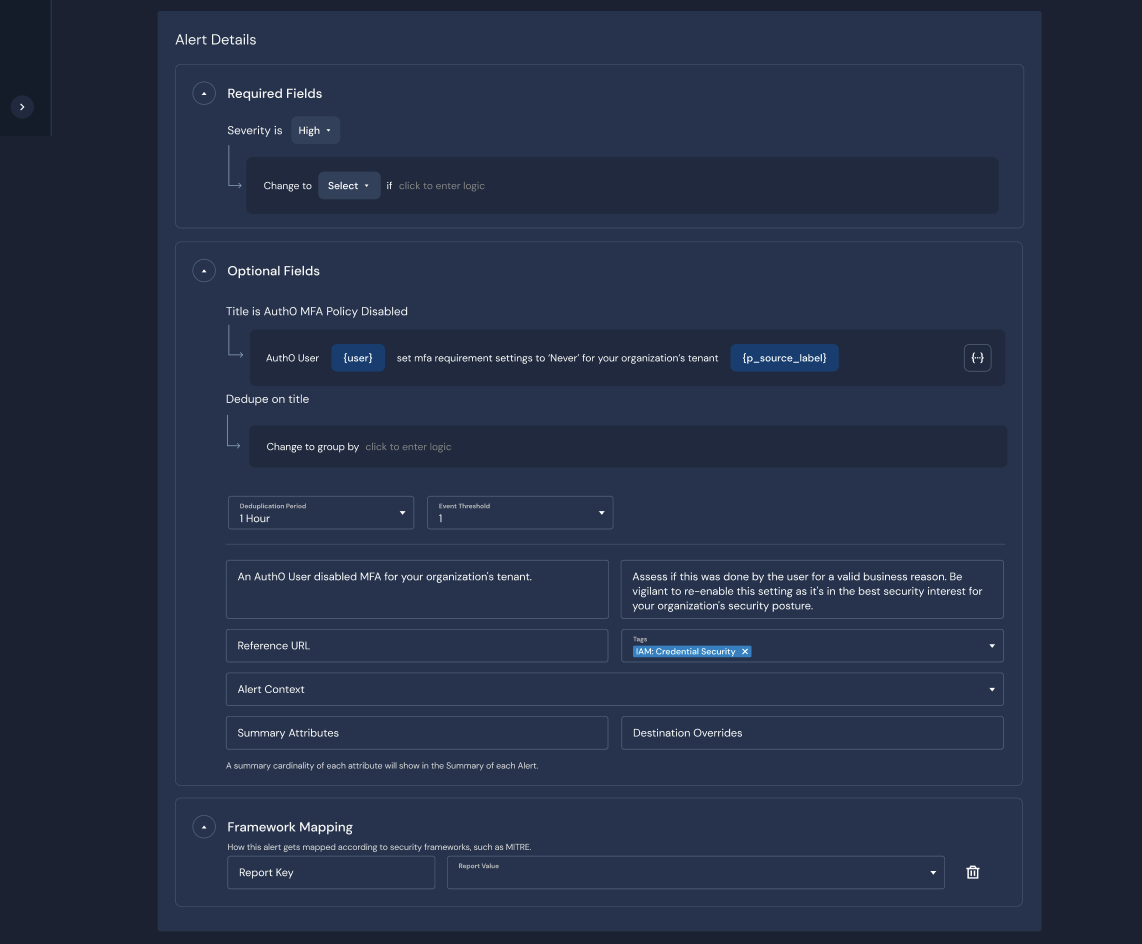
Users managing detections through the developer workflow will soon have the option to write YAML-based rules or customize Panther-managed rules. We will provide migration tools for the Panther-managed rules if you would like to take advantage of the inheritance benefits of Simple Detections.
We will continue to publish new detections and detection updates in Python, in the panther-analysis repository. Soon, inline filters can be applied to Python-based rules to make simple modifications such as allow or deny lists. This mirrors the Rule Filters that are available in the Console today.
YAML-based detections can live in your detections repository alongside Python-based ones and all be uploaded using the Panther Analysis Tool (PAT).
Panther will always enable the most powerful aspects of Detection-as-Code, but we also want support teams on their journey towards the new paradigm. In order to help security teams progress towards a developer-centric approach, Panther’s product will provide a bridge from GUI-based actions to writing detections in code and using developer tools like CI/CD workflows.
We’re excited to shape Panther into a platform where each team member has the best tools available to get their job done, while easily collaborating with others. By bridging console and developer workflows, all team members can manage detections using either interface based on their preference – increasing team efficiency and accelerating detection development and tuning.
If you’d like to learn more about Simple Detections, please register for our technical deep-dive webinar in July or request a demo of the Panther platform.
