At Panther, we meticulously analyze recent cyber attacks and emerging threats, sharing our insights with the security community. Our expert analysts work tirelessly to respond to threats, providing you with tools and information to defend your systems. We also offer specific recommendations and detections to mitigate and prevent intrusions or attacks.
Our latest research focuses on social engineering attacks exploiting Okta infrastructure, impacting MGM, Caesars, and over 30 properties worldwide. With identity providers like Okta becoming prime targets, understanding the methods of threat actors like the Scattered Spider group is crucial. We’ll share key findings and steps to detect and combat these threats effectively.
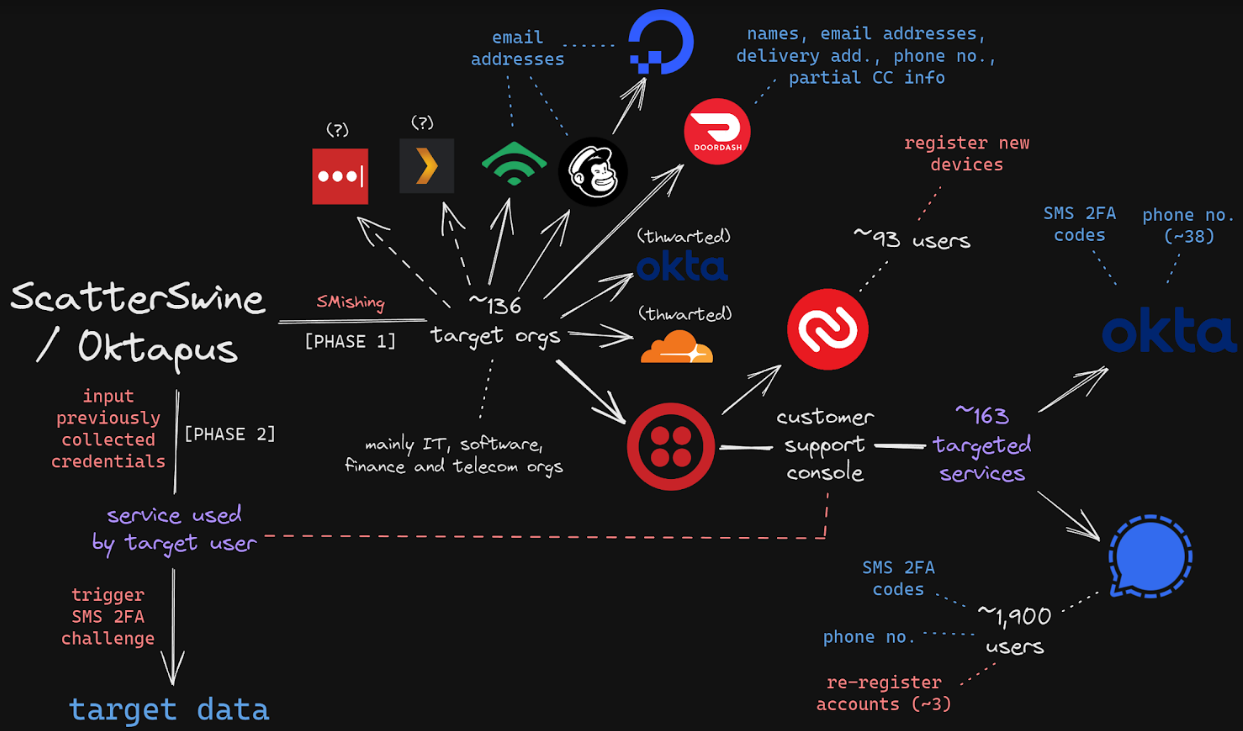
The Scattered Spider threat actor group is believed to be comprised of English-speaking, financially motivated individuals in the US and UK. The group is known for deploying social engineering schemes to trick users into handing over their login credentials and is tracked as an affiliate for the BlackCat/ALPHV ransomware. Group-IB dubbed the gang by a different name — 0ktapus — a nod to how the criminal group phished employees for Okta credentials. Scattered Spider’s activities overlap with other intrusion activities like Scatter Swine, UNC3944, Octo Tempest, Muddled Libra, and many others. As of February 2024, the victims of Scattered Spider include Zendesk, Walmart, LinkedIn, Costco, Grubhub, Gitlab, Apple, Allstate, and many others.
In Q4 2023, Scattered Spider performed a series of high-profile attacks against MGM Resorts, Caesar’s, and others using sophisticated social engineering techniques [T1566.004] to pose as employees [T1656] and gain access to those organizations’ Okta admin consoles.
These attacks targeted Okta customers, typically initiating with either an SMS phishing message, or “Smishing,” to harvest credentials, or via an old-school (yet still highly effective) social engineering vishing call, aiming to obtain credentials or persuade the target to download malicious software and grant access.
Threat actors seemed to possess either a) passwords for privileged user accounts or b) the ability to manipulate the delegated authentication flow via Active Directory (AD) before contacting the IT service desk at a targeted organization, requesting a reset of all MFA factors in the target account. In the case of Okta customers, the threat actor focused on users assigned Super Administrator permissions. It is reasonable to assume that attackers will utilize valid accounts for lateral movement.
According to Okta, during their MGM attack, the threat actor accessed the compromised account using anonymizing proxy services and an IP and device not previously associated with the user account. The compromised Super Administrator accounts were utilized to assign higher privileges to other accounts and reset enrolled authenticators in existing administrator accounts [TA0004]. In some instances, the threat actor removed second-factor requirements from authentication policies.
Subsequently, the threat actor was observed configuring a second Identity Provider to function as an “impersonation app” to access applications within the compromised Org on behalf of other users. This second Identity Provider, also controlled by the attacker, would act as a “source” IdP in an inbound federation relationship (sometimes referred to as “Org2Org”) with the target. They were able to maintain persistence even after account passwords were changed [T1078].
From this “source” IdP, the threat actor manipulated the username parameter for targeted users in the second “source” Identity Provider to match a real user in the compromised “target” Identity Provider. This granted the ability to Single sign-on (SSO) into applications in the target IdP as the targeted user.In collaboration with the BlackCat/ALPHV ransomware gang, they leveraged their unrestricted access to the victims’ SSO providers to pivot [TA0008] into other systems in those environments to exfiltrate sensitive data [TA0010] and deploy ransomware [T1486].
It is crucial for organizations to closely monitor and detect new Tactics, Techniques, and Procedures (TTPs) in the Okta audit logs to identify any suspicious activities and potential security breaches. In response to the attacks and ongoing activity, Panther has deployed 7 new real-time detections in Github. If you are a Panther customer or testing our product, please refer to and leverage these recent detections.
If you are not currently a Panther customer, please take a moment to review the detection logic and familiarize yourself with the recommended approach, as these tactics are becoming more widespread, and the threat actors continue to operate, despite an arrest on January 30th in Florida of one of the individuals believed to be involved.
Check out this recent webinar where Panther’s Ken Westin, Field CISO, and Ariel Ropek, principal threat Researcher at Panther Threat Research Labs discuss the the importance of monitoring Okta, rigorous detection testing via Purple Teaming, and the latest in Panther’s managed detections.
Stay tuned for upcoming threat research where we will focus on Cloud Cryptojacking and cloud ransomware, and – of course – provide rapid response research to public breaches and security incidents.
