Nation-State Actors Targeting Software Supply Chain via GitHub
Ken
Westin
Aug 2, 2023
GitHub has warned developers of a social engineering operation targeting developers in the cryptocurrency, gambling, and cybersecurity industries. The "Lazarus Group" is a well-known and notorious hacking group linked to North Korea. This group has been involved in numerous high-profile cyberattacks, including financial theft, espionage, and destructive attacks. Lazarus is also known as "Jade Sleet" by Microsoft and "TraderTraitor" by CISA.
The Lazarus Group is believed to be backed by the North Korean government and is known for its sophisticated cyber capabilities. They have been responsible for various cyber incidents, such as the 2014 Sony Pictures hack, the 2016 Bangladesh Bank heist, and recently several attacks on cryptocurrency exchanges.
Anatomy of a Social Engineering Software Supply Chain Attack
The Lazarus Group's latest attack path is taking aim at organization's software supply chain through a nefarious social engineering campaign targeting developers as illustrated in Figure 1. The attackers leverage existing or fake social media profiles on LinkedIn, Slack, and Telegram to make contact with their developer targets. The social engineering approach is used to gain their target's trust and convince them to collaborate on software projects such as media players and cryptocurrency tools; they then send them a link to a code repository (both private and public) to clone and execute.
When the developer runs the code, it calls out to install malicious node package manager dependencies, which act as first-stage malware loaders which then load second-stage malware to the system. All of the malicious code is deployed from remote systems. Phylum provides a more detailed description of the malicious NPM packages. GitHub provides a list of IoCs, such as the NPM packages, domain names, and associated GitHub accounts used in the campaign.
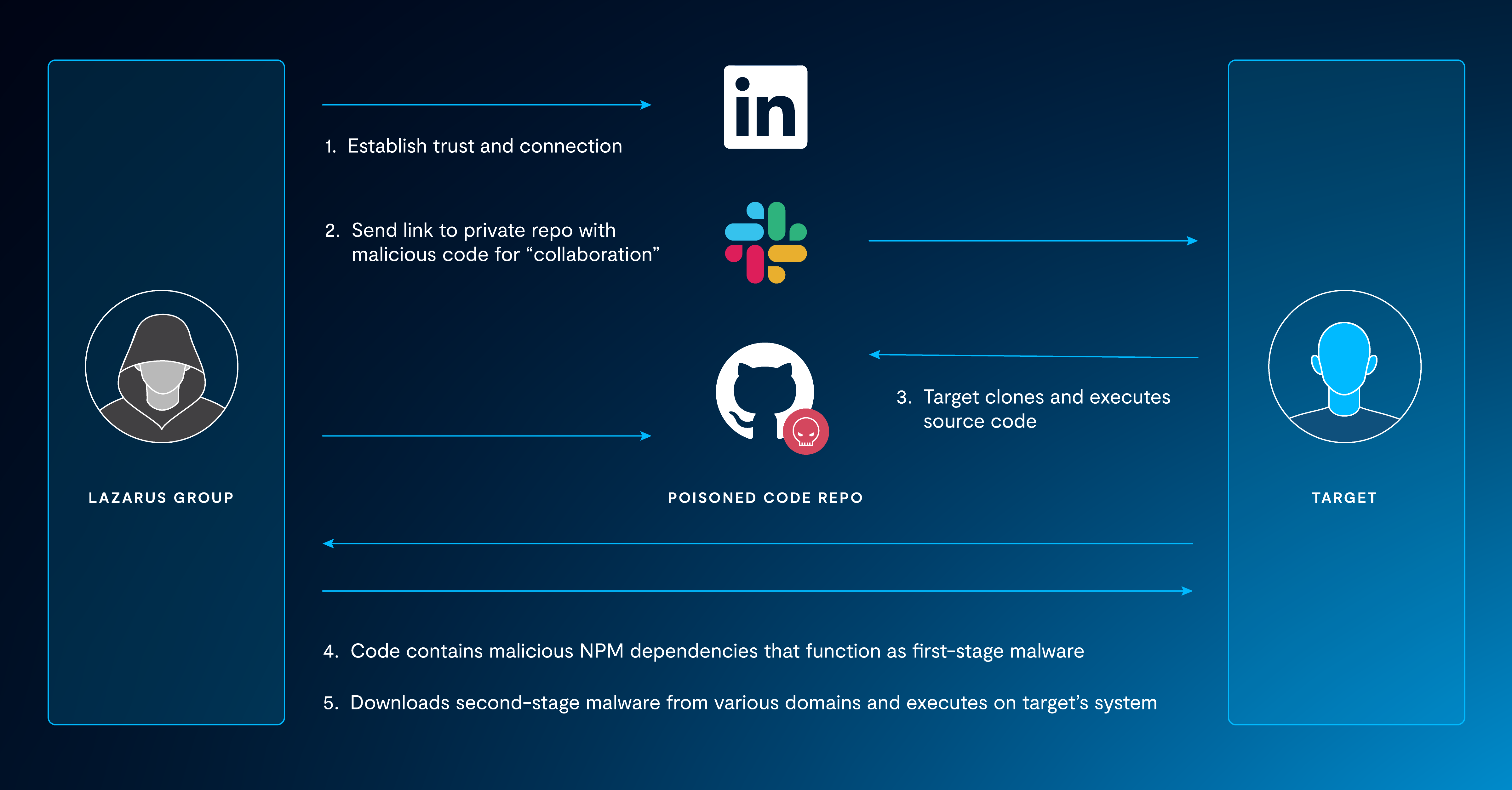
Figure 1. Lazarus Group Attack Sequence Targeting GitHub Users
Remediation
It is recommended that if a GitHub user believes they may have been targeted, they review their personal GitHub Logs to see if they accepted an invite from any of these malicious user accounts:
GalaxyStarTeam
Cryptowares
Cryptoinnowise
Netgolden
Suppose the malicious code from the target repository was cloned and executed. In that case, additional steps to wipe the machine should be performed, as well as reset any credentials on the system which may have been compromised. The Lazarus Group appears to be targeting cryptocurrency and gambling sites to gain access to crypto wallets, while they may be targeting cybersecurity companies to install back doors or gain credentials to gain access to their customers downstream.
The Software Supply Chain Threat
Adversaries know that many organizations are moving more and more of their operations to the Cloud and increasingly developing their own applications, particularly in the financial and cybersecurity realm. This shift requires organizations to shift their risk models to the left, where they are logging and analyzing security data for threats to their internal network and employee endpoints and securing their DevOps and Cloud environments. There has not only been an uptick in the frequency of these types of attacks but also in the severity of their impact, as they often involve the initial entity being attacked and their downstream customers, whether it is commercial software or an open-source tool. Organizations should not only be logging traditional security data from firewalls, endpoints, etc. but also their DevOps and Cloud environments.
Panther will be running a virtual workshop on Aug 22 from 11 AM - 1 PM (PDT), "Code to Cloud: Securing the Software Supply Chain with Detection-as-Code and Modern SIEM," where we will run a series of hands-on labs focused specifically on threats to the software supply chain. This workshop will focus on log sources not usually ingested into legacy SIEMs such as GitHub, Okta, and AWS Cloudtrail and how we can identify and mitigate common threats to an organization's software supply chain. I will also give a talk at Black Hat on Thursday, Aug 10, 2023, at 12:40 PM in the room "Mandalay Bay L." on Securing the Software Supply Chain with Detection-as-Code.' I hope to see you at an event soon!
Share:





