Maximizing Endpoint Security with SentinelOne and Panther
Brandon
Min
Jan 26, 2023
Endpoint Detection and Response (EDR) solutions are used to record and store endpoint-system-level behaviors such as file/registry changes, service start/stop, inter-process communications, and network activity. Products within this industry typically use various data analytics techniques to analyze the actions above.
One of the leading EDR solutions is SentinelOne (S1). S1 provides insight into the organization's endpoint context and event logs to detect activities like malware installation or data exfiltration. This blog will discuss the new integration between SentinelOne and Panther and highlight how it can secure your organization's endpoints.
Detect malicious URLs faster
Let's take an example where an employee gets phished via a suspicious link on their laptop. This user is new to the organization and hasn't set up multi-factor authentication or other IAM security measures, giving the intruder easy access to numerous company applications. If the user interacts with any potentially malicious URLs, S1 will log this data and flag them as possible phishing attacks.
Within the Panther tool, a security engineer can use ingested S1 data and run an indicator search to correlate common IoCs against all log sources in their environment.
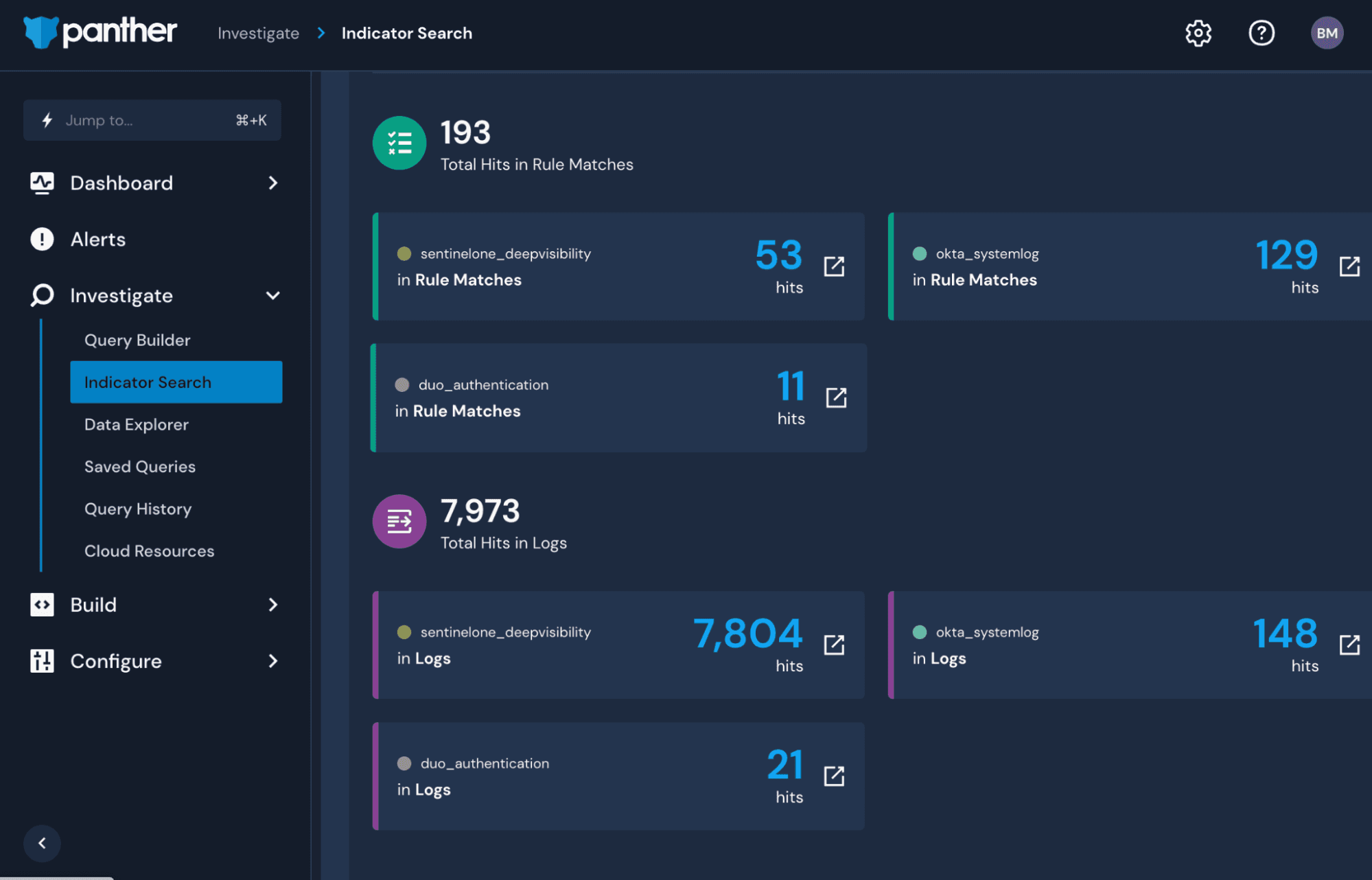
With the results, you can now see the rule matches and log hits associated with the potentially malicious URLs reported by S1 across all log types. Seeing that there are many hits in Okta, you can dig deeper into the information using a simple SQL query. This can be generated automatically from an indicator search by clicking on the respective box.
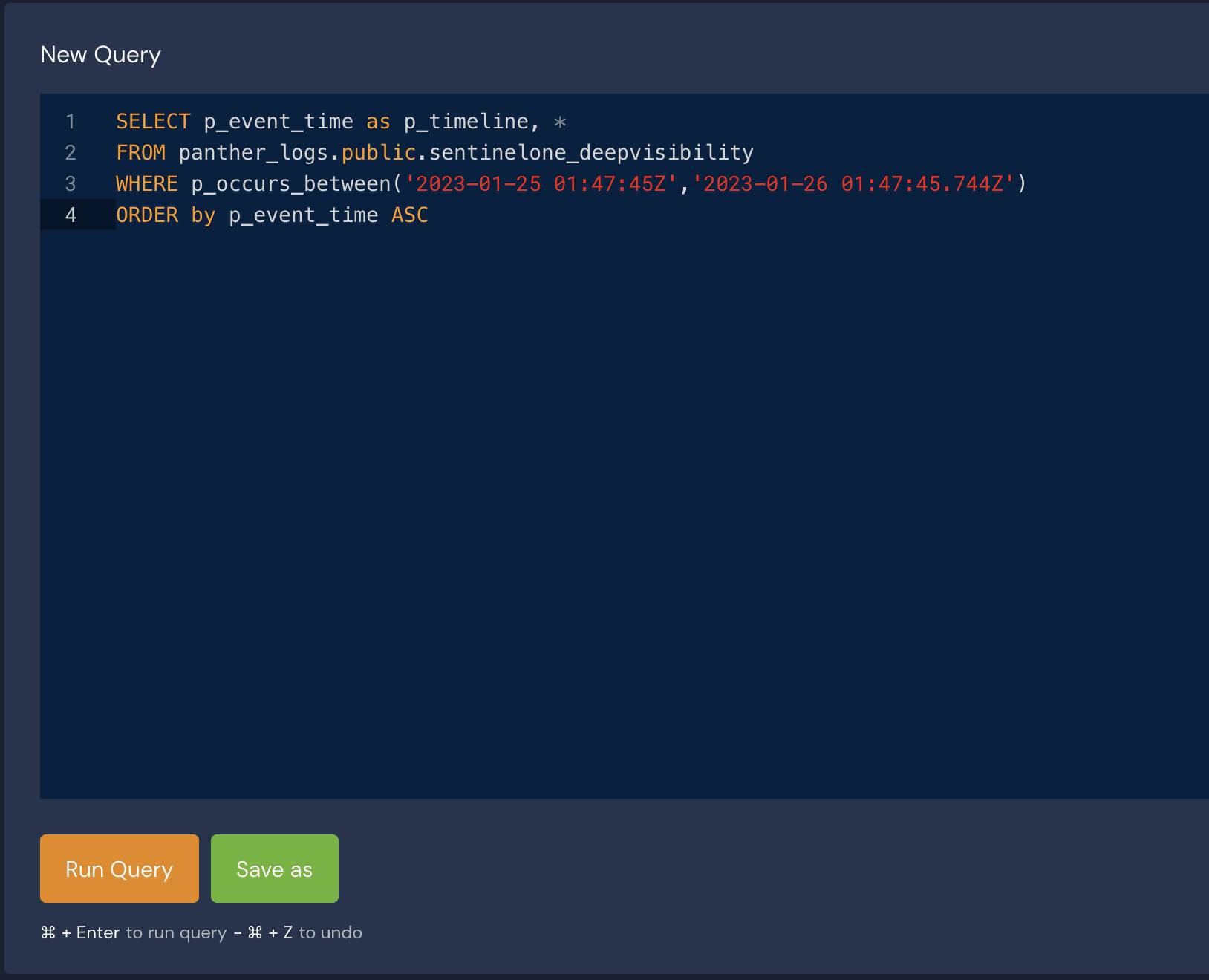
You can quickly pivot from event logs, correlate it with the rest of your environment, and analyze the suspected findings with other services. This gives you a complete understanding of the potential threat within minutes of beginning your search.
Integrating SentinelOne API with Panther
To integrate the SentinelOne API with Panther, login to your SentinelOne console and generate an API Token. The instructions for this walkthrough can be found in our documentation.
Once completed, you'll need to share the API Token value with Panther. Login to the Panther console and navigate to Configure > Log Source > Create. Search for SentinelOne API' and select Start Source Setup.'
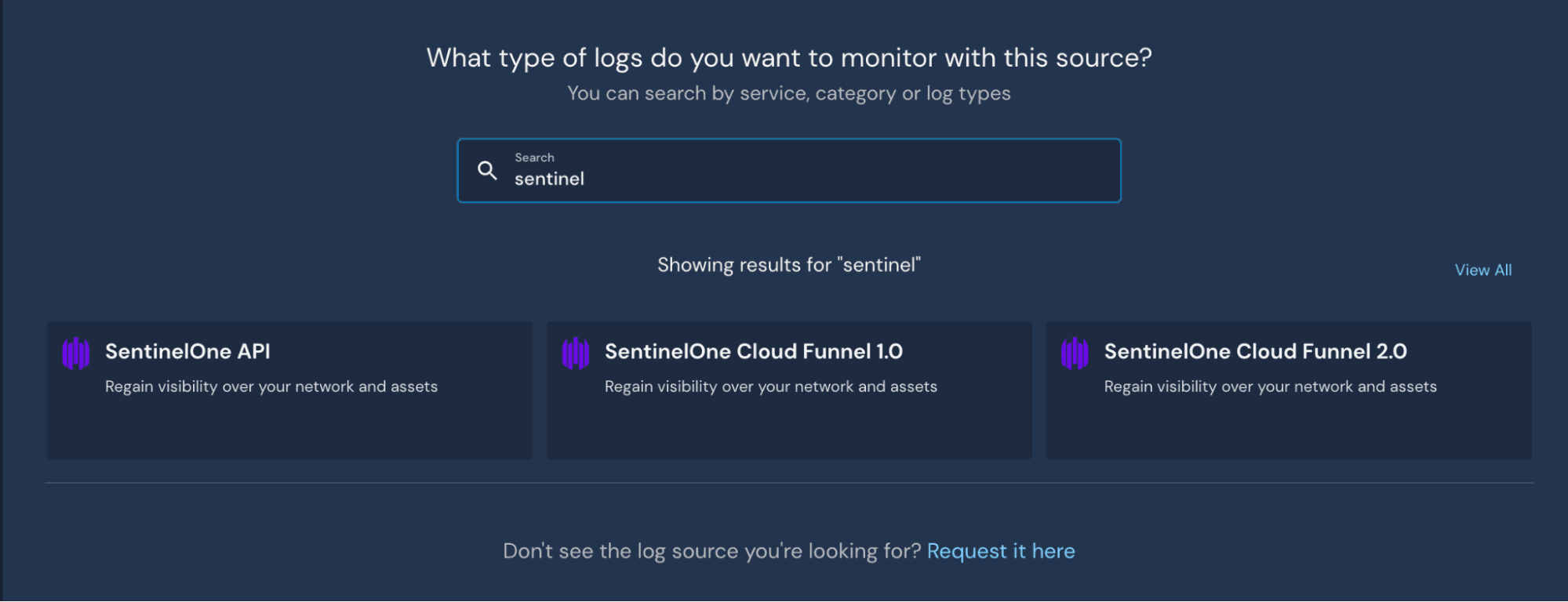
On the following screen, you'll name your integration and share your SentinelOne API Organization URL and API Token. The associated schema is already pre-populated so that event logs can stream in immediately. Select 'Setup' when completed. The setup is now complete. The API integration will allow you to analyze SentinelOne API activity logs with custom-made Python detections.
Integrating SentinelOne CloudFunnel with Panther
Panther supports CloudFunnel v1.0 and v2.0 for ingesting logs from S1's Deep Visibility product. Deep Visibility provides real-time telemetry data from endpoints and servers to help security teams correlate activity and search for lateral movements. This information can be critical in Panther as teams can add enrichment, context, and correlation with non-S1 logs. To integrate CloudFunnel v2.0, follow S1's documentation to send S1 logs to S3, then utilize Panther's documentation to connect S3 to Panther. Once the respective S3 bucket parameters are shared in the Panther console, the logs will be ingested with the schema already applied.
*We currently offer support for CloudFunnel v1.0 but note that SentinelOne will deprecate this method in May 2023.
Supported SentinelOne Products
Panther can now integrate with the following SentinelOne products:
API Activity Logs
Deep Visibility via Cloud Funnel v1
Deep Visibility via Cloud Funnel v2
These data sources have pre-built schema provided out-of-the-box in the Panther product. Once integrated with S1, logs can be automatically parsed, normalized, and enriched as they're streamed into Panther. Users can then create detections to apply to event logs in real-time and get alerts within minutes.
Get Started
With the ability to set up Panther in under an hour, security teams can immediately add coverage of SentinelOne. Our platform provides teams with more detection coverage, development efficiency, and accuracy with alerts and can also lead to significant reductions in the total cost of ownership.
Share:





