Adopting Real-Time Threat Detection Workflows
Brandon
Min
Sep 30, 2022
The security industry's average time to detect a breach is 207 days.
This is primarily attributed to security teams using outdated threat detection methods and clunky legacy SIEM tools. How can any organization expect to stay ahead of the ever-changing threat landscape when they're behind a potential intruder by Oi of a year? The bottom line is traditional threat detection practices are no longer viable. They only provide an incomplete answer due to the heavy lead time required to operate legacy SIEM tools, making it difficult for security teams to address critical security questions efficiently and effectively.
This is why real-time threat detection is empowering security teams to flip the script on potential intruders. Real-time threat detection is the evolution of traditional threat detection that utilizes best-in-class modern security tools to analyze potential threats instantly. In the case of modern SIEM tools, teams can automate analysis to occur directly as event logs are ingested.
You may be thinking: it must take years to develop an appropriate real-time threat detection strategy and months to deploy a modern SIEM tool. In this blog, we'll address how to adopt a real-time threat detection strategy with modern SIEM in under an hour.
We'll also address the following questions:
What is real-time threat detection?
What can modern SIEM with real-time threat detection provide a security team?
How to leverage real-time threat detection in Panther
What is Real-Time Threat Detection?
Real-time threat detection is the practice of analyzing event data for malicious activity the instant it's generated by the event source. Traditionally, this has been done using a SIEM tool that can aggregate logs to a single place, and enable security engineers to write detections that signal alerts when a vulnerability or threat occurs.
SOC's can trigger alerts about potential intruders in minutes rather than days and weeks and lowers security teams' mean time to detect (MTTD) and mean time to respond (MTTR). This is accomplished by running threat analysis at the point of ingesting rather than in batches or by indexing data, creating far less lead time to receiving an alert. However, real-time threat detection practices are still not commonly adopted due to the continued usage of legacy SIEM tools.
Why do legacy SIEM tools lead to slow MTTD?
Traditionally, threat detection has been a static approach where business data is converted to security data and analyzed by a legacy SIEM tool. This is commonly executed in batches of data that need to be indexed before analysis, preventing data from being analyzed as soon as it's generated by an application, infrastructure, or network source.
When data is ingested from a specified log source, the data needs to be parsed and normalized to be analyzed within a SIEM tool. These parsers can take weeks to create and must be made for every respective log source. Once completed, detections must be written to analyze the incoming logs. However, detection creation is no easy process in legacy SIEMs that leverage proprietary languages and lack detection-as-code workflows. Sometimes detections can take weeks or even months to develop, and may not necessarily trigger properly from the start.
Once this is completed, a team can finally begin to index data and run it through their detection pipeline to alert on potential threats. This process means that MTTD can be as much as weeks or even months. This hampers security teams from fully protecting their organization, but a modern SIEM with real-time threat detection can flip the script for a SOC.
Real-Time Threat Detection in Panther
With a modern SIEM tool like Panther, real-time threat detection becomes available to all security teams right from the start. The tool was created to analyze logs at the point of ingestion in order to provide instant analysis. Security engineers can create Python-based detections in minutes to run on incoming data and alert on potential threats.
The process begins by setting up log ingestion from a supported log or through a data transport within Panther. Once logging begins, data is parsed and normalized automatically and then stored in AWS S3. Panther then runs a real-time detection engine against the logs that are within S3. This includes all of the enabled out-of-the-box rules or custom rules created by a security team that applies to the ingested log source. If a detection is triggered, it will fire off an alert. If not, it will pass over to the next detection.
With this process, an engineer can potentially receive an alert less than 5 minutes after the original log was generated in its source. Let's walk through how to get this set up for yourself.
Setting up Real-Time Threat Detection & Alerting in Panther
Once you've received access to the Panther console, you can immediately begin by setting up different log sources to ingest data. The easiest way to get started is with either a cloud service like AWS or GCP, or with an API-based source such as Okta, 1Password, or Crowdstrike. Most API-based sources take under 10 minutes to set up by simply creating an API token and sharing it in the Panther console. Steps are laid out for each integration in our documentation.
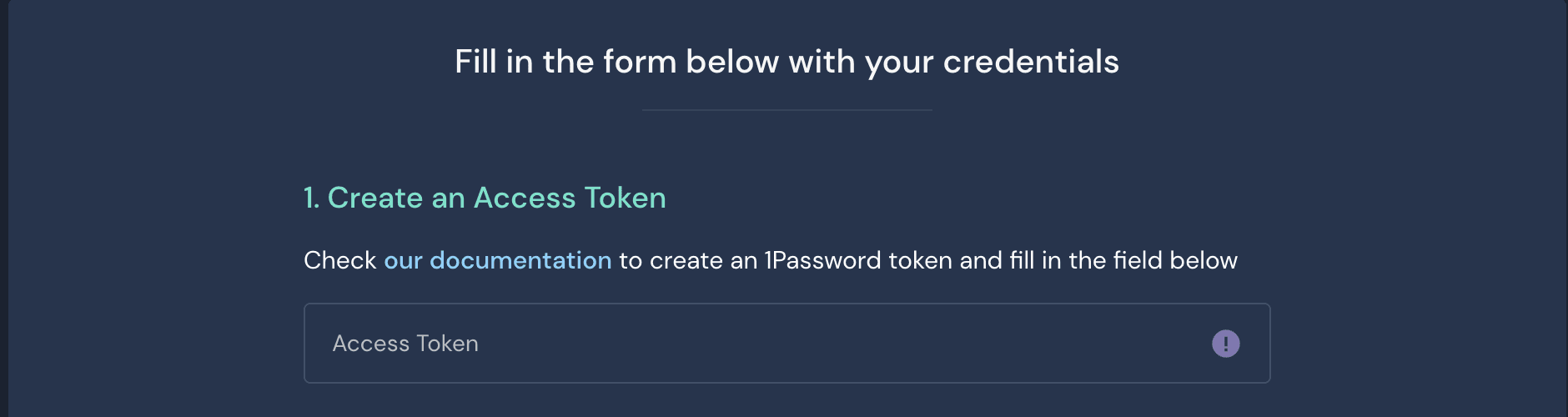
Once the source is logging properly, you can either enable a detection pack provided out-of-the-box by Panther or begin to write your own detections in the console or locally with the Panther Analysis Tool. The fastest way is to enable a pack that can be located directly in the console under Build > Packs. If we onboarded 1Password logs, there will be a specified pack in correlating to that log source.

Once enabled, detections will analyze log data as it's being sent into Panther. The last step in this process is setting up an alert destination in which you and your team can receive alerts. This can be set up in the Panther Console by selecting Configure > Alert Destinations > Create New and then selecting the source you'd like to set up. The full list of supported sources can be found below.
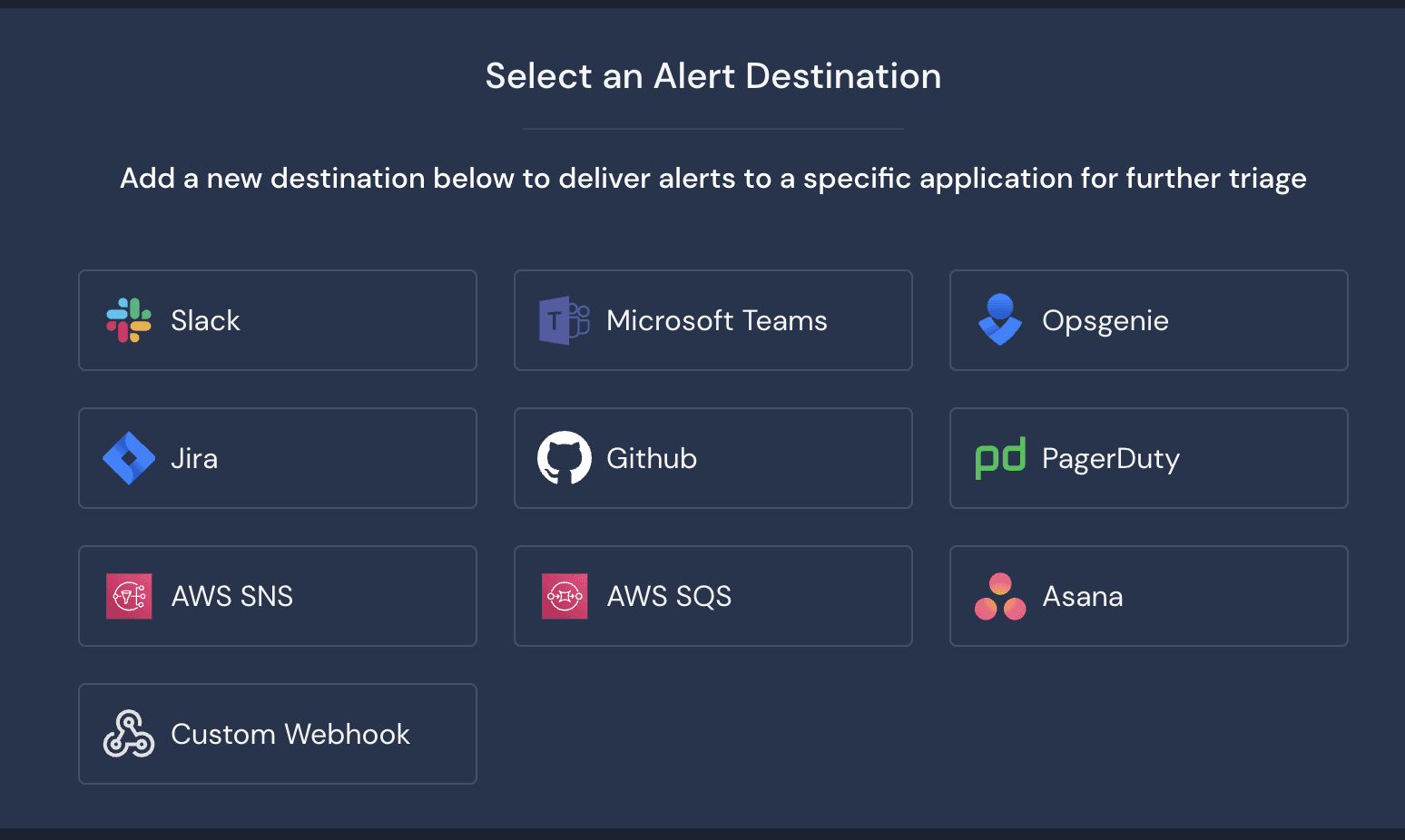
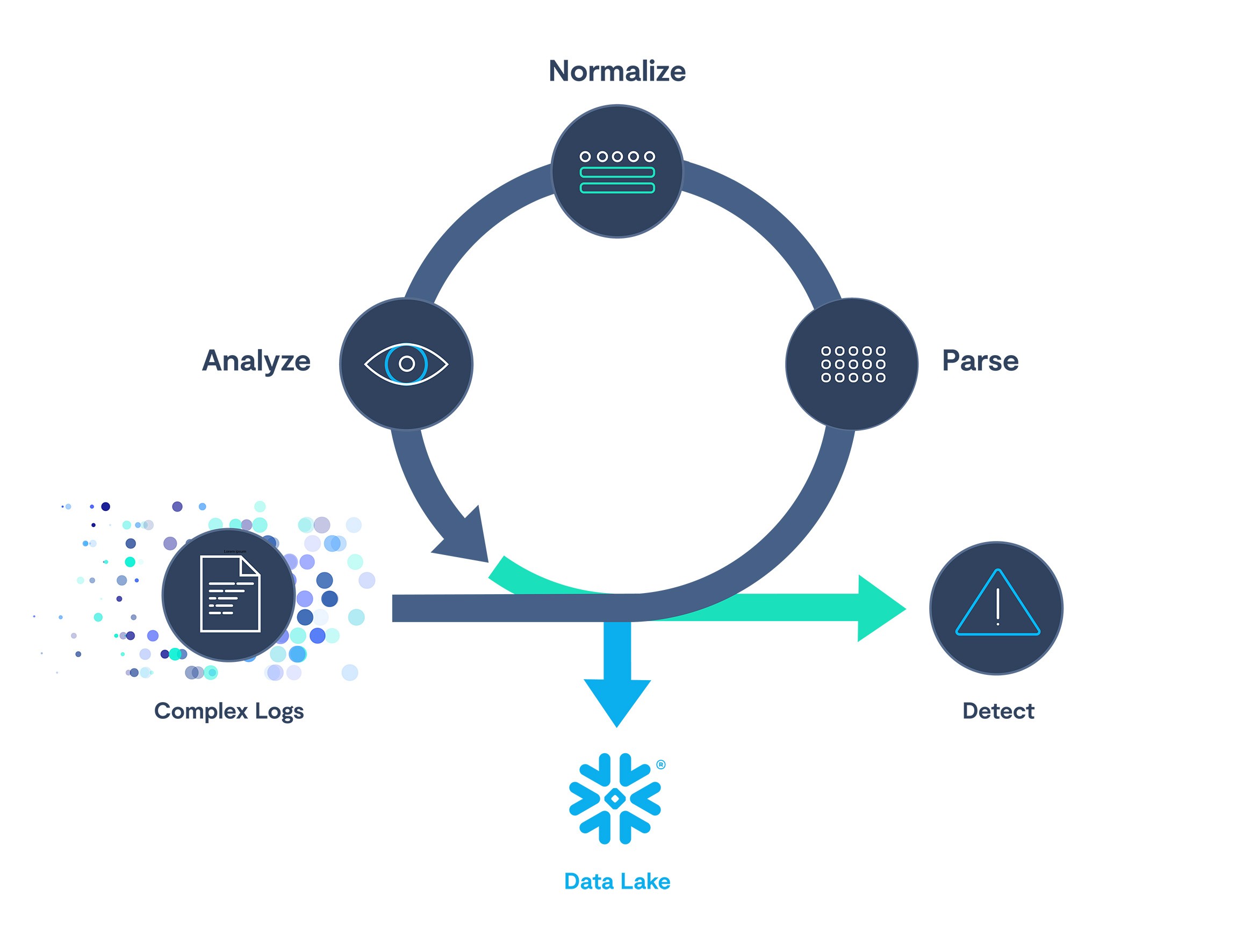
When this is completed, you now have coverage of the log source that you integrated, and you will have enabled instant real-time threat detection and alerting of that source in your environment. The following graphic recaps the flow we just discussed:
Get Started
With the ability to set up Panther in under an hour, security teams have immediate access to add real-time threat detection to their organization. Our platform provides teams with more detection coverage, development efficiency, and accuracy with alerts, and can also lead to significant reductions in total cost of ownership.
Recommended Resources
Ready for less noise
and more control?
See Panther in action. Book a demo today.





